- @blibla@slrpnk.net English
- •
- github.com
- •
- 3d
- •
- @BodaciousMunchkin@links.hackliberty.org English
- •
- aeon.co
- •
- 7d
- •
- @ForgottenFlux@lemmy.world English
- •
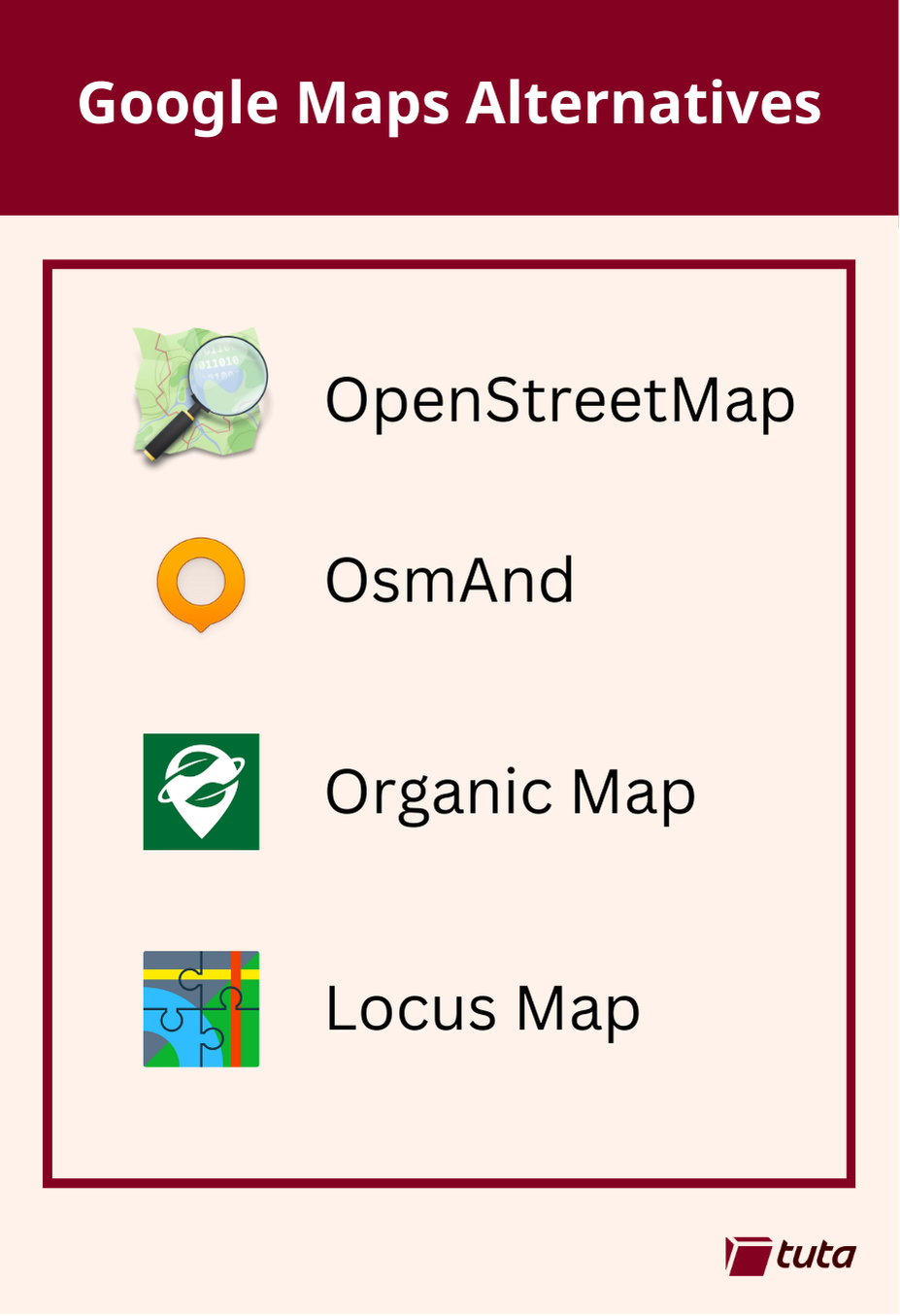
- tuta.com
- •
- 8d
- •
 English
English- •
- 8d
- •

- •
- 14d
- •
@privacyguides collaborators, it’s time to review the recommendation of Firefox as a good browser option…
- @ForgottenFlux@lemmy.world English
- •
- www.techradar.com
- •
- 14d
- •
 English
English- •
- www.eff.org
- •
- 21d
- •
- @ForgottenFlux@lemmy.world English
- •
- techcrunch.com
- •
- 21d
- •
- @ForgottenFlux@lemmy.world English
- •
- techcrunch.com
- •
- 1M
- •
- @TheTwelveYearOld@lemmy.world English
- •
- 1M
- •
- @TheTwelveYearOld@lemmy.world English
- •
- 1M
- •
- Elven_Mithril English
- •
- 1M
- •
- @pcouy@lemmy.pierre-couy.fr English
- •
- pierre-couy.dev
- •
- 2M
- •
- @ForgottenFlux@lemmy.world English
- •
- www.techzine.eu
- •
- 2M
- •
- @fine_sandy_bottom@lemmy.federate.cc English
- •
- 2M
- •

- •
- 2M
- •
 English
English- •
- grapheneos.social
- •
- 2M
- •
- @TheTwelveYearOld@lemmy.world English
- •
- 2M
- •
Google ads push fake Google Authenticator site installing malware | The ad displays “google.com” and “https://www.google.com” as the click URL, and the advertiser’s identity is verified by Google
- @ForgottenFlux@lemmy.world English
- •
- tuta.com
- •
- 3M
- •
- @ForgottenFlux@lemmy.world English
- •
- apnews.com
- •
- 3M
- •
 English
English- •
- 3M
- •
- @CaptObvious@literature.cafe English
- •
- 3M
- •
- @ForgottenFlux@lemmy.world English
- •
- techcrunch.com
- •
- 3M
- •
- @ForgottenFlux@lemmy.world English
- •
- arstechnica.com
- •
- 3M
- •
- @ForgottenFlux@lemmy.world English
- •
- techcrunch.com
- •
- 3M
- •
- @diy@sh.itjust.works English
- •
- 3M
- •
- @TheTwelveYearOld@lemmy.world English
- •
- 3M
- •
- @TheTwelveYearOld@lemmy.world English
- •
- 3M
- •
- @TheTwelveYearOld@lemmy.world English
- •
- 3M
- •
- @TheTwelveYearOld@lemmy.world English
- •
- 3M
- •
 English
English- •
- www.buskill.in
- •
- 3M
- •
- @TheTwelveYearOld@lemmy.world English
- •
- 3M
- •
Privacy Guides
!privacyguides@lemmy.oneIn the digital age, protecting your personal information might seem like an impossible task. We’re here to help.
This is a community for sharing news about privacy, posting information about cool privacy tools and services, and getting advice about your privacy journey.
You can subscribe to this community from any Kbin or Lemmy instance:
Check out our website at privacyguides.org before asking your questions here. We’ve tried answering the common questions and recommendations there!
Want to get involved? The website is open-source on GitHub, and your help would be appreciated!
This community is the “official” Privacy Guides community on Lemmy, which can be verified here. Other “Privacy Guides” communities on other Lemmy servers are not moderated by this team or associated with the website.
Moderation Rules:
- We prefer posting about open-source software whenever possible.
- This is not the place for self-promotion if you are not listed on privacyguides.org. If you want to be listed, make a suggestion on our forum first.
- No soliciting engagement: Don’t ask for upvotes, follows, etc.
- Surveys, Fundraising, and Petitions must be pre-approved by the mod team.
- Be civil, no violence, hate speech. Assume people here are posting in good faith.
- Don’t repost topics which have already been covered here.
- News posts must be related to privacy and security, and your post title must match the article headline exactly. Do not editorialize titles, you can post your opinions in the post body or a comment.
- Memes/images/video posts that could be summarized as text explanations should not be posted. Infographics and conference talks from reputable sources are acceptable.
- No help vampires: This is not a tech support subreddit, don’t abuse our community’s willingness to help. Questions related to privacy, security or privacy/security related software and their configurations are acceptable.
- No misinformation: Extraordinary claims must be matched with evidence.
- Do not post about VPNs or cryptocurrencies which are not listed on privacyguides.org. See Rule 2 for info on adding new recommendations to the website.
- General guides or software lists are not permitted. Original sources and research about specific topics are allowed as long as they are high quality and factual. We are not providing a platform for poorly-vetted, out-of-date or conflicting recommendations.
Additional Resources:
- 1 user online
- 1 user / day
- 30 users / week
- 68 users / month
- 826 users / 6 months
- 1 subscriber
- 662 Posts
- 11.1K Comments
- Modlog
Lemmy.one
The better front page of the internet
Lemmy.one is a general-purpose instance of Lemmy, a self-hostable, decentralized alternative to Reddit and other link aggregators. Learn more…
To save on server-storage, please consider using third-party providers like imgur if you want to post images, thanks!
For the best experience, set your default post type to “All” and your default sort type to “Hot” in your profile settings.
Community creation is disabled on Lemmy.one, so if you’re hoping to do that you should probably register your account on a different Lemmy instance. Learn more…
Some communities to check out first:
Tech → !technology@beehaw.org
News → !news@beehaw.org
Memes → !memes@sopuli.xyz
Music → !music@beehaw.org
Books → !literature@beehaw.org
What are the rules here?
- No pornography.
- No racism, sexism, homophobia, transphobia, xenophobia, or casteism
- No incitement of violence or promotion of violent ideologies
- No harassment, dogpiling or doxxing of other users
- No content illegal in the United States, Germany, or Finland
- Do not share intentionally false or misleading information
- Do not spam or abuse network features.
Operating this server costs money, if you’d like to support the service, please consider contributing on Ko-Fi or Patreon. Thank you!