

WardPearce
Open source developer & privacy advocate.
- 8 Posts
- 32 Comments
Isn’t just a theme, is a completely different application built on top of Invidious’ API. What works completely differently to Invidious’ current UI. A LOT of things are handled different then how Invidious handles it on their frontend. Replacing Invidious current interface with Materialious isn’t a good idea, because its quite a bit bigger & requires JS compared to Invidious’ current UI.
Calling Materialious a theme would be like calling clipious a theme.
Yea, Materialious is a bit more complex then a theme as it has a lot of custom client side logic (Like sync parties, playlists, etc).
If I expanded Materialious you’d still be able to use just Invidious or Safetwitch etc.
But Materialious at its core would still be built off the API of giants. So it wouldn’t be reinventing the wheel for scrapping/handling data from twitch, YouTube etc.
Haven’t used Proxitok in a while, so not sure if its working currently. Seems to be in active development tho. Misspoken, doesn’t appear to be working & hasn’t been updated in awhile


Material design 3 was released in 2021, so I’d call that somewhat modern and is the latest release of Material design. Unlike Apple’s design language Material design is also meant for the web.
There is already a Invidious interface for Apple devices, but ofc isn’t a web interface like Materialious.

 English
English- •
- lemmy.nz
- •
- 6M
- •

 English
English- •
- 9M
- •


Basically think of it as a SDK for defining data deletion on a platform. Omitme handles all the annoying stuff like account storage, building a CLI/GUI & sessions.
The core of Omitme is Seleniumwire used to grab login session tokens for platforms & HTTPX for making requests with those session tokens. Then you simply define you data deletion “targets” and the API calls to delete such data.

 English
English- •
- github.com
- •
- 1Y
- •




Agreed, should have an alart for missed canaries. Each canary has “statements” you publish new statements to update ur canary. This provides a signed record of passed canaries.
Browser extension or even mobile app could be another aspect of further securing validation. Currently we do store a offline backup for each public key in idb storage & a signed copy if you have a account for further validation if the URL hash has been tampered with.
Thank you for your kind words ❤️❤️

 English
English- •
- lemmy.nz
- •
- 1Y
- •


I’d love to be covered in your blog, feel free to add me on Matrix if you have any questions.

 English
English- •
- lemmy.nz
- •
- 1Y
- •


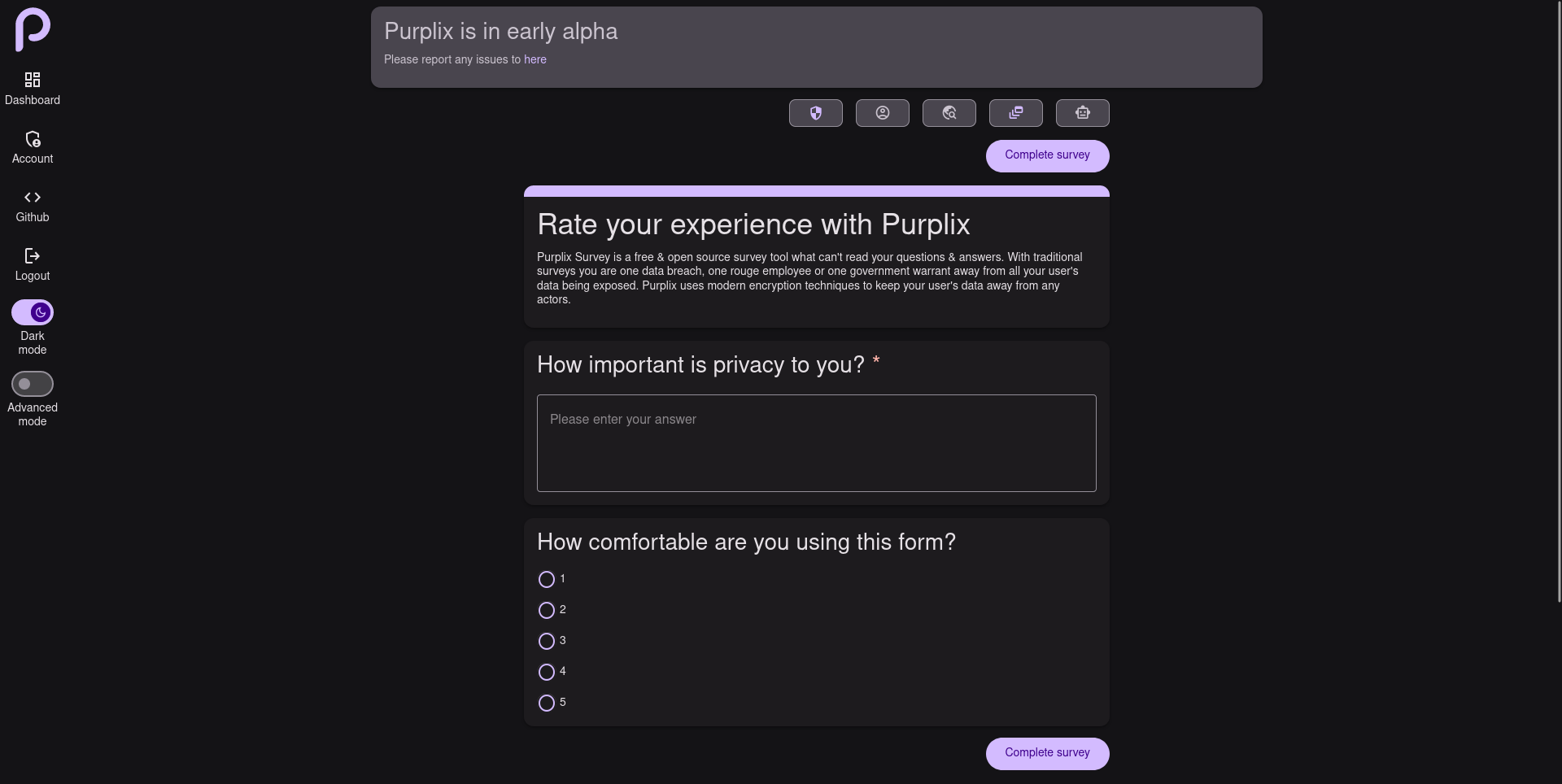
Not 100% sure what you mean, but the encryption key for questions are only known by users who are shared the link & is never transmitted to the server. Answers are encrypted by the survey’s public key what only the creator of said survey knows the private key. The public key is also encrypted by the secret key in the URL so the server can’t even submit answers.
Here is a example URL of a survey.
s/64b185662c74e7c40cac5e66- This is the survey ID, transmitted to server./KfcrkxiR-4nomGbEqNos0dyhEBsgiUAqPpZiRQt5syE- This is a hash of the survey’s signing public key, this is to stop MITM attacks from the host & validation of the survey questions.#oAnQnjWhxq2IFTZBvrylVSHxg92HoWQr2mJQ-qZwvPY- This is the secret key for decrypting questions, this is also used to decrypt the public key for encrypting answers. This key is never transmitted to server.
All encryption & decryption happens locally, so the server never sees any plain text. It is possible for the host to modify the frontend to expose keys, but this is true of any web app & Purplix is hosted from Vercel straight from our Git repo, so it would be quite obvious if this happened.


No not currently, not comfort taking funding for any of my projects right now, until I establish some sort of expensive breakdown and transparent fund use. But even with funding a decent audit from a company who knows what they are doing would probably be 7k USD minimum.
I do have a personal fund for hosting, what is used for Paaster. https://github.com/sponsors/WardPearce


E2EE meaning survey questions and answers are encrypted locally & decrypted locally. The server or any other actors can’t view survey questions aside from users its shared with and survey answers are only readable by the owner of such survey.
This means on a data leak, nothing is readable.
Yea Purplix.io is still in development, so it isn’t live yet. Hense the fail DNS lookup you show.

 English
English- •
- github.com
- •
- 1Y
- •
Using a KDF for stateless passwords is a interesting concept. It isn’t prefect tho. What if you want multiple passwords for one site, lack of any 2FA, KDF has to be somewhat fast (bcrypt or scrypt what takes under a second) & once your master password gets leaked your screwed (compared to cloud stored passwords with 2FA, key rotation etc)
Realistically stateless password managers suffer from the same attacks cloud based ones do, MITM attacks. If the client is open to being tampered with, your keys can always get leaked.
Ente’s auth app is a good option too.





It requires the Invidious instance to have the correct COR values for Materialious, but yes connects to a existing instance.